Introduction
Understanding the critical role of E-Discovery in litigation, investigations, and compliance is essential in the digital age. Relevant Data Technologies specializes in providing end-to-end E-Discovery services that are pivotal in identifying and processing critical data. This guide explores the various facets of their services, emphasizing how they can transform legal outcomes through advanced technology and expert handling.
Section 1: Relativity Data Hosting and Managed Solutions
1.1 Relativity Data Hosting
What is Relativity hosting?
Benefits of Relativity Data Hosting for large-scale litigation
Key features of Relativity hosting services provided by Relevant Data Technologies
Relativity Data Hosting: Enhancing E-Discovery for Large-Scale Litigation
In the complex landscape of legal proceedings, the importance of efficient data management cannot be overstated. Relativity hosting emerges as a pivotal solution in this context, offering robust features tailored to streamline the process of electronic discovery (E-Discovery). Relevant Data Technologies stands at the forefront of this field, providing exceptional Relativity hosting services that cater specifically to the demands of large-scale litigation.
What is Relativity Hosting?
Relativity hosting refers to the use of the Relativity software platform via a hosted, cloud-based solution. Relativity is a comprehensive E-Discovery tool that facilitates the process of legal review, helping law firms, corporations, and government entities to manage large volumes of data effectively. Hosting Relativity in the cloud offers enhanced accessibility, scalability, and security, allowing legal teams to focus on the litigation process without the added concern of managing physical IT infrastructure.
Relativity provides an array of tools for data processing, review, and analysis, making it an indispensable asset for any legal entity dealing with extensive datasets and complex legal challenges. When hosted, Relativity allows users to access these powerful tools through the internet, leveraging cloud computing’s flexibility and efficiency.
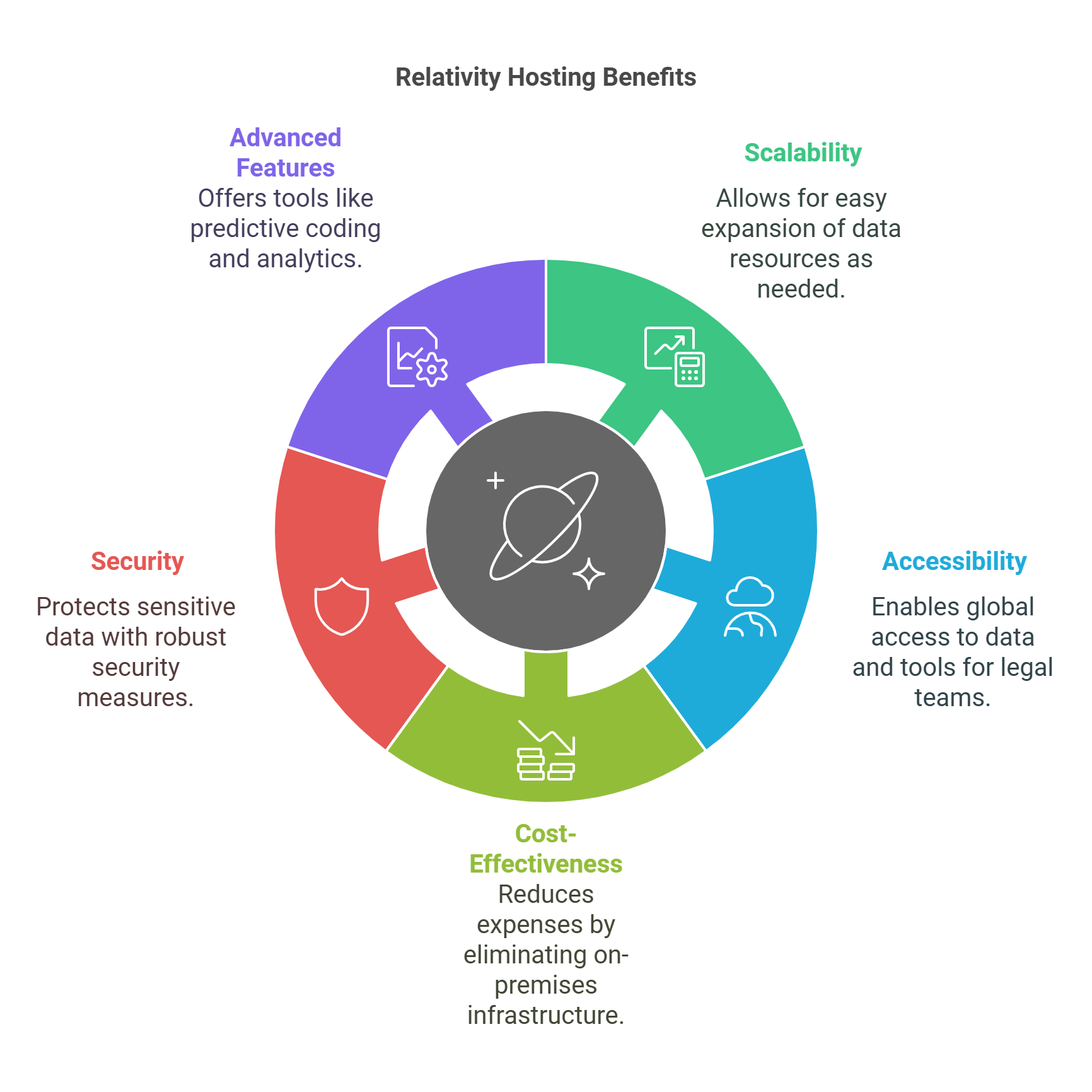
Benefits of Relativity Data Hosting for Large-Scale Litigation
Scalability: One of the primary benefits of Relativity data hosting is its scalability. Legal cases can often grow unexpectedly in scope, necessitating a flexible approach to data management. Relativity hosting can easily scale up resources to accommodate increasing data volumes without the need for significant hardware investments, ensuring that legal teams can continue to operate efficiently regardless of case size.
Accessibility: With Relativity hosted in the cloud, legal teams can access their data and tools from anywhere in the world. This is particularly beneficial for large-scale litigations involving multiple parties across different geographies. Lawyers, paralegals, and experts can collaborate seamlessly, accessing case materials and tools consistently and securely.
Cost-Effectiveness: Maintaining on-premises servers for E-Discovery processes can be prohibitively expensive, especially when dealing with large volumes of data. Relativity hosting services eliminate the need for extensive physical infrastructure, reducing capital expenditure and minimizing ongoing maintenance costs.
Security: Large-scale litigation often involves sensitive data that requires the highest levels of security. Relativity hosting provides robust security measures, including data encryption, secure access protocols, and comprehensive compliance with legal and regulatory standards. This ensures that all data remains secure from unauthorized access and breaches.
Advanced Features: Hosting Relativity offers advanced features like predictive coding and advanced analytics, which can significantly speed up the review process and reduce the workload on legal teams. These tools use machine learning algorithms to help identify relevant documents quickly and accurately, a crucial advantage in large-scale litigation where time and accuracy are of the essence.
Key Features of Relativity Hosting Services Provided by Relevant Data Technologies
Relevant Data Technologies offers a suite of specialized features within its Relativity hosting services, designed to optimize the E-Discovery process:
Managed Relativity Solutions: Recognizing the unique needs of each client, Relevant Data Technologies provides managed Relativity solutions that include customized workflows, specific security settings, and tailored data management strategies to enhance efficiency and compliance.
Cloud-Based E-Discovery Hosting: By leveraging cloud technologies, Relevant Data Technologies ensures that all hosted data is easily accessible yet securely managed. This includes regular data backups, disaster recovery options, and strict adherence to data protection laws, which are essential for managing legal data.
Expert Support and Consultation: With a deep understanding of both the technical and legal aspects of E-Discovery, Relevant Data Technologies offers expert support and consultation services. This includes everything from initial setup and migration to ongoing support and training for legal teams to maximize their use of the Relativity platform.
Integration Capabilities: Understanding that E-Discovery often involves using multiple tools and data sources, Relevant Data Technologies ensures that its Relativity hosting services are fully compatible with a variety of data formats and third-party applications. This integration capability facilitates a smoother workflow and a more cohesive E-Discovery process.
In conclusion, the Relativity hosting services provided by Relevant Data Technologies offer not just a tool but a comprehensive solution that addresses the specific challenges of large-scale litigation. By combining advanced technology with expert support, Relevant Data Technologies ensures that its clients can handle complex legal challenges efficiently, securely, and cost-effectively.
1.2 Managed Relativity Solutions
Customizing Relativity to meet client needs.
Case study on the efficiency of Managed Relativity solutions
Managed Relativity Solutions: Customizing E-Discovery to Client Needs
In the realm of legal proceedings, where the volume and complexity of data can be overwhelming, having a tailored approach to E-Discovery is crucial. Managed Relativity solutions offered by Relevant Data Technologies provide a specialized adaptation of the Relativity platform, ensuring that it aligns perfectly with the unique requirements of each client. This approach not only enhances the efficiency of the legal review process but also ensures that firms can handle their E-Discovery needs more effectively and with greater precision.
Customizing Relativity to Meet Client Needs
Relativity is renowned for its robust capabilities in handling extensive data sets and complex legal analysis. However, the one-size-fits-all model doesn’t always align with the specific needs of every legal firm or corporate legal department. Herein lies the significance of managed Relativity solutions—customizing the platform to suit particular client requirements and workflows.
Personalization: At Relevant Data Technologies, personalization is key. The firm understands that each client has different needs based on the nature of their cases, the type of data involved, and their operational workflows. Whether it’s adjusting the Relativity environment to provide enhanced data visualization tools or configuring specific user permissions and security settings, each setup is meticulously crafted to align with the client’s operational ethos and case demands.
Workflow Optimization: One of the most critical aspects of customization involves streamlining and optimizing workflows within Relativity. This can include automating repetitive tasks, setting up specific document review protocols, and integrating custom plugins that enhance functionality. By optimizing these workflows, legal teams can significantly reduce the time and effort spent on manual tasks, focusing instead on strategic analysis and decision-making.
Security Customization: Given the sensitivity of legal data, security customization is a cornerstone of managed Relativity solutions. Relevant Data Technologies implements advanced security measures tailored to the security posture and compliance requirements of each client. This can range from encrypted data storage and secure access controls to comprehensive audit trails and compliance with international data protection regulations.
Case Study on the Efficiency of Managed Relativity Solutions
To illustrate the effectiveness of managed Relativity solutions, consider the case of a large law firm specializing in corporate litigation. The firm faced significant challenges managing the vast amounts of data involved in multiple ongoing cases, which impacted their ability to perform timely and accurate document reviews.
Client Challenge: The law firm’s existing E-Discovery tools were inadequate, leading to inefficient data processing and a backlog of cases that needed urgent review. The firm required a solution that could not only handle large volumes of data but also streamline their review process to improve case handling efficiency.
Solution Implemented: Relevant Data Technologies was brought on board to provide a managed Relativity solution. The first step involved a thorough assessment of the firm’s specific needs, including the types of cases handled, the nature of the data involved, and the internal team dynamics. Based on this assessment, Relevant Data customized the Relativity setup to enhance its data processing capabilities and tailor the review workflow to reduce bottlenecks.
Custom workflows were designed to automate document tagging and categorization, which were previously done manually. Additionally, a series of custom reports were created to give team leaders real-time insights into the review process, enabling better management of resources and timelines.
Results: The implementation of the managed Relativity solution transformed the firm’s E-Discovery process. Document review times were reduced by 40%, and the accuracy of data categorization improved significantly, leading to faster case resolutions and higher client satisfaction. The firm was able to handle a higher volume of cases without additional resources, effectively increasing their return on investment in the Relativity platform.
Conclusion
Managed Relativity solutions by Relevant Data Technologies exemplify the integration of technology with client-specific customization to deliver efficient and effective E-Discovery processes. By tailoring Relativity to meet the precise needs of clients, Relevant Data ensures that law firms and corporate legal departments can leverage the full power of E-Discovery to drive better legal outcomes. This case study demonstrates not just the adaptability of Relativity when managed correctly but also highlights the potential for significant efficiency gains in the demanding arena of legal data management.
1.3 Cloud-based E-Discovery Hosting
Advantages of cloud solutions in E-Discovery
Security measures and compliance with legal standards
In the ever-evolving landscape of legal technologies, cloud-based E-Discovery hosting stands out as a transformative solution for law firms, corporate legal departments, and government agencies. This approach not only enhances the efficiency and scalability of legal operations but also ensures rigorous compliance with security and legal standards. Let’s explore the multiple advantages of cloud solutions in E-Discovery and the critical security measures that uphold its integrity and reliability.
Advantages of Cloud Solutions in E-Discovery
Scalability and Flexibility: One of the most significant benefits of cloud-based E-Discovery hosting is its scalability. Legal cases can vary drastically in size and complexity, often expanding unexpectedly as they progress. Cloud hosting allows legal teams to scale their data storage and processing capabilities on demand, without the need for upfront investments in physical infrastructure. This flexibility is crucial during times of fluctuating caseloads, enabling legal professionals to adapt quickly to new requirements.
Cost Efficiency: Cloud solutions offer a more cost-effective model for E-Discovery by eliminating the need for large capital expenditures on hardware and IT infrastructure. Instead, firms can leverage a pay-as-you-go model where they only pay for the storage and services they use. This not only reduces initial investment costs but also lowers ongoing maintenance and upgrade expenses, as these are managed by the cloud service provider.
Enhanced Collaboration: Cloud-based E-Discovery facilitates better collaboration among dispersed legal teams. As data is stored centrally in the cloud, team members can access and work on the same files simultaneously, regardless of their physical location. This capability is particularly beneficial in large-scale litigation involving multiple stakeholders or in cases where experts from various geographies need to collaborate closely.
Accessibility and Mobility: With data hosted in the cloud, legal professionals can access case materials anytime and from anywhere, provided they have internet access. This level of accessibility enhances productivity and allows lawyers to continue working on cases outside of traditional office settings—critical in today’s increasingly mobile and flexible working environments.
Security Measures and Compliance with Legal Standards
Data Security Protocols: Security is a paramount concern in legal data management, particularly when sensitive and confidential information is involved. Cloud providers offering E-Discovery hosting implement robust security protocols to protect data. These measures include data encryption at rest and in transit, secure authentication mechanisms, and the use of firewalls and intrusion detection systems to guard against unauthorized access.
Compliance and Certifications: Cloud providers must comply with various legal and regulatory standards to ensure that the data hosted on their platforms meets the stringent requirements of the legal industry. This includes adhering to standards such as ISO 27001 for information security management, HIPAA for the protection of personal health information, and GDPR for data protection and privacy in the European Union. Compliance with these standards is critical to protect client data and avoid legal liabilities.
Regular Audits and Updates: To maintain security and compliance, cloud providers conduct regular audits and updates of their systems. These audits are performed to ensure that all security measures are up to date and effective against emerging threats. Updates and patches are applied as necessary to mitigate vulnerabilities, ensuring that the cloud environment remains secure against new types of cyberattacks.
Data Sovereignty and Localization: Legal data often falls under specific jurisdictional laws that dictate how and where data should be stored and processed. Cloud providers typically offer data localization solutions to ensure that data is stored in specific regions as required by law, thereby adhering to legal mandates concerning data sovereignty.
Conclusion
Cloud-based E-Discovery hosting represents a forward-thinking approach to managing the complexities and demands of modern legal cases. By leveraging the cloud, legal teams can enjoy enhanced scalability, cost efficiency, collaboration, and mobility—all underpinned by stringent security measures and adherence to legal standards. As law firms and corporate legal departments continue to navigate the challenges of data-intensive legal processes, cloud solutions provided by reputable providers like Relevant Data Technologies offer not just technological solutions but strategic advantages in a competitive field. The adoption of cloud-based E-Discovery hosting is not merely an operational decision; it’s a strategic move towards smarter, more secure, and responsive legal practices.
1.4 Relativity SaaS Provider
Integrating Relativity as a Service (SaaS) in legal practices
Enhancing accessibility and collaboration through SaaS solutions
In the dynamic world of legal proceedings where data is pervasive and decisive, the integration of robust technological solutions like Relativity Software as a Service (SaaS) can significantly enhance the operational efficiency of legal practices. As a leading Relativity SaaS provider, Relevant Data Technologies has been at the forefront of transforming legal processes by making advanced E-Discovery tools accessible and collaborative through cloud-based solutions. This comprehensive discussion delves into how integrating Relativity as a Service can revolutionize legal practices, focusing on its impact on accessibility and collaboration.
Integrating Relativity as a Service (SaaS) in Legal Practices
Streamlined Deployment and Management: One of the core advantages of Relativity SaaS is the simplicity it brings to deployment and management. Legal firms no longer need to invest in complex infrastructure or manage software installations and updates. As a SaaS provider, Relevant Data Technologies handles all aspects of deployment, maintenance, and upgrades, ensuring that the Relativity platform is always up-to-date with the latest features and security standards. This turnkey solution allows law firms to focus more on their core legal activities rather than on IT management.
Scalability and Flexibility: Relativity SaaS offers unmatched scalability, crucial for managing fluctuating caseloads in legal practices. Whether a case requires expansive data ingestion or involves a limited dataset, Relativity can scale to meet diverse needs without the upfront cost of additional hardware or long-term commitments. This flexibility is particularly beneficial for legal practices handling cases of varying sizes and complexities, enabling them to tailor their resources according to specific case demands.
Cost Efficiency: Cost management is a significant consideration for any legal practice. Relativity SaaS models provide a cost-effective solution by eliminating the need for large capital investments in hardware and software. Instead, law firms can utilize a subscription-based model that offers predictable costs and includes regular updates and support. This not only helps in budget management but also reduces the overall total cost of ownership of the technology.
Enhancing Accessibility and Collaboration through SaaS Solutions
Anywhere, Anytime Access: In today’s globalized legal environment, the ability to access data and collaborate from anywhere is indispensable. Relativity SaaS provides cloud-based access to the platform, enabling legal professionals to work from any location at any time. This is particularly advantageous for teams that operate across different geographies or need to travel frequently. Lawyers can review documents, tag evidence, and prepare case files whether they are in the office, in court, at home, or traveling, ensuring that case progress is not hindered by physical boundaries.
Enhanced Collaboration: Legal cases often require collaboration among various stakeholders, including attorneys, paralegals, forensic experts, and clients. Relativity SaaS enhances collaboration through real-time data sharing and communication tools integrated within the platform. Team members can simultaneously access case data, make annotations, and share insights, significantly improving the speed and efficiency of document reviews and legal analyses. This collaborative environment also supports transparency and improves the accuracy of the work, as revisions and inputs are tracked and synchronized in real time.
Security and Compliance: While cloud accessibility offers numerous advantages, it also brings challenges related to data security and compliance with legal standards. As a Relativity SaaS provider, Relevant Data Technologies ensures that all data hosted on the platform adheres to stringent security protocols, including data encryption at rest and in transit, secure authentication mechanisms, and regular security audits. Additionally, compliance with legal and regulatory requirements is a top priority, ensuring that data handling meets all jurisdictional laws and ethical standards, which is crucial for maintaining the integrity of legal processes.
Integration Capabilities: Another significant advantage of Relativity SaaS is its ability to integrate with other legal and business tools. This interoperability allows for a seamless workflow where data from various sources can be easily imported into Relativity. Whether it’s integrating with case management software, billing systems, or advanced analytics tools, the ability to connect systems reduces data silos and enhances process efficiency.
Conclusion
The integration of Relativity as a Service by Relevant Data Technologies marks a significant advancement in the field of legal E-Discovery. Offering a combination of flexibility, scalability, and cost-efficiency, alongside enhanced accessibility and collaboration features, Relativity SaaS is transforming how legal practices manage and analyze vast amounts of case-related data. By adopting this sophisticated cloud-based solution, legal firms can not only improve their operational efficiencies but also gain a competitive edge in the fast-paced legal landscape, ensuring they provide the best possible service to their clients.
Section 2: Data Processing Techniques
2.1 E-Discovery Data Processing
Overview of data processing in the context of E-Discovery
How data processing impacts the discovery phase in litigation
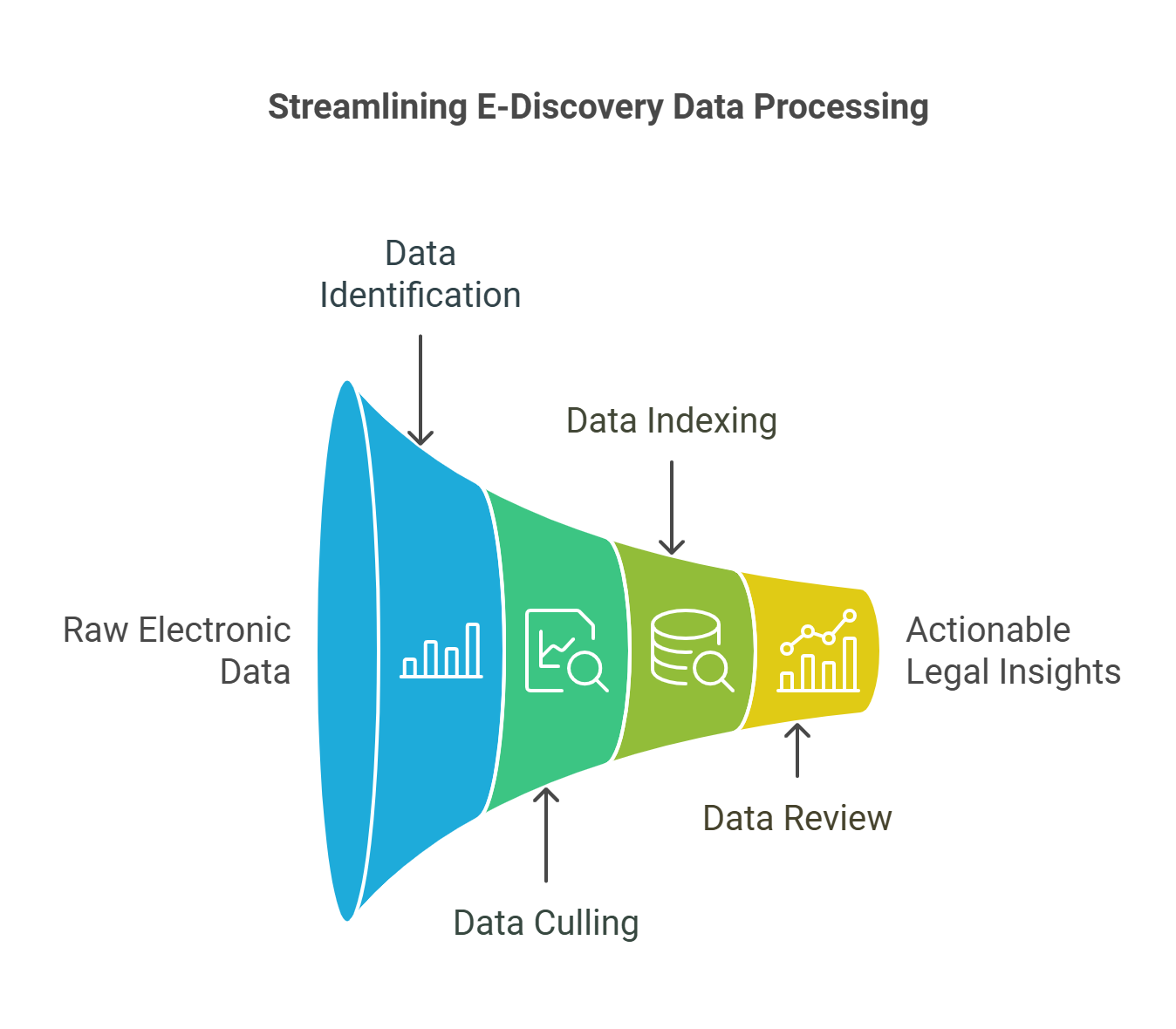
In the landscape of modern litigation, the significance of electronic discovery (E-Discovery) cannot be overstated. As legal proceedings increasingly hinge on digital data, the efficiency of the E-Discovery process plays a pivotal role in determining the success of legal outcomes. At the core of E-Discovery lies data processing—a critical phase that transforms raw data into actionable insights. Relevant Data Technologies specializes in offering comprehensive E-Discovery data processing services, tailored to enhance the discovery phase in litigation. This article provides an in-depth overview of data processing within the context of E-Discovery and examines its profound impact on litigation.
Overview of Data Processing in the Context of E-Discovery
Definition and Importance: Data processing in E-Discovery involves the collection, preparation, and management of electronic data for the purpose of legal review and analysis. This phase is critical because it determines the quality and usability of data, which can ultimately influence the litigation process. Data processing includes several key steps: identification, preservation, collection, processing, review, analysis, and production of electronic documents. Each step must be meticulously executed to ensure data integrity and relevance.
Techniques Employed: The data processing stage employs various advanced techniques to handle and organize large volumes of data efficiently. These techniques include:
Data Culling: Using parameters such as date ranges, specific keywords, and document types to reduce the volume of data that needs to be reviewed.
De-duplication: Removing duplicate copies of documents to streamline the review process and reduce costs.
Email Threading: Grouping email conversations in threads to maintain context and continuity, which enhances the review process.
Data Conversion: Converting data into formats suitable for review and analysis, often involving text extraction and metadata preservation.
Tools and Technologies: Leveraging cutting-edge technologies is crucial in E-Discovery data processing. Relevant Data Technologies utilizes state-of-the-art software and tools that ensure precision and efficiency. These tools support various data formats and sources, ensuring comprehensive data capture and transformation. The integration of artificial intelligence and machine learning also enhances the capabilities of these tools, allowing for smarter data processing and anomaly detection.
How Data Processing Impacts the Discovery Phase in Litigation
Streamlining Data Review: Efficient data processing significantly streamlines the review phase by organizing data into manageable chunks and prioritizing relevant documents. This not only speeds up the review process but also reduces the workload on legal teams, allowing them to focus on strategic aspects of the case.
Reducing Costs: The costs associated with reviewing large volumes of data can be prohibitive. Effective data processing techniques minimize the volume of data presented for review, which directly translates to lower costs. Techniques such as de-duplication and email threading can dramatically decrease the number of documents to be reviewed, offering substantial cost savings.
Enhancing Data Quality: Quality data processing ensures that the data used in legal proceedings is accurate, relevant, and complete. This enhances the reliability of the data, which is crucial for building strong cases. Properly processed data reduces the risk of overlooking critical information or encountering data errors during the trial.
Meeting Compliance and Deadlines: In litigation, meeting compliance standards and deadlines is non-negotiable. Efficient data processing helps legal teams adhere to regulatory requirements related to data handling and privacy. Moreover, it ensures that all discovery materials are prepared and submitted within the stipulated timelines, thereby avoiding legal penalties or case dismissals.
Facilitating Better Legal Strategies: High-quality data processing provides a clearer picture of the available evidence, which is instrumental in formulating effective legal strategies. It enables legal professionals to identify trends, patterns, and relationships within the data, which can be pivotal in crafting arguments or negotiating settlements.
Conclusion
The role of data processing in E-Discovery is integral and transformative. By employing advanced data processing techniques, Relevant Data Technologies ensures that legal professionals have access to accurate, relevant, and efficiently organized data. This not only streamlines the discovery phase but also significantly impacts the overall efficacy and cost-efficiency of litigation. As legal cases continue to grow in complexity and scale, the demand for sophisticated E-Discovery data processing solutions will only increase, reinforcing the need for expertise and innovation in this crucial area of legal practice.
2.2 Legal Data Culling
Techniques used in data culling to reduce volume and enhance relevance
Importance of effective data culling in reducing costs and time
In the intricate world of legal proceedings, managing the vast volumes of data involved in E-Discovery can be daunting and expensive. Legal data culling stands as a critical phase in the E-Discovery process, designed to reduce the volume of data and enhance its relevance, thus ensuring a more efficient review process. This essential task not only helps in managing resources more effectively but also plays a significant role in shaping the outcomes of litigation by focusing on the most pertinent information. This article delves into the techniques used in legal data culling and underscores the importance of effective data culling in reducing costs and time in legal processes.
Techniques Used in Data Culling to Reduce Volume and Enhance Relevance
Data culling is the process of systematically reducing the volume of data to be reviewed in legal cases without losing relevant information. It involves various techniques and technologies, each tailored to sieve through large datasets to retain only what is most likely relevant to the case. Here are some of the most effective techniques:
Keyword Searching: One of the most common culling techniques involves the use of specific keywords, phrases, or Boolean queries to search through documents. This method relies on predefined criteria relevant to the case, which can significantly narrow down the dataset to manageable proportions.
Date Range Filtering: Limiting documents to a certain date range relevant to the litigation can effectively reduce the volume of data. This technique is particularly useful in cases where the timeline of events plays a crucial role in the matters at hand.
De-duplication: This involves removing duplicate copies of documents. De-duplication can be done at various levels—within a specific custodian’s data set or across all data in the litigation. This not only reduces the volume but also prevents reviewers from spending time on reviewing multiple copies of the same document.
Email Threading: This technique identifies and groups emails that are part of the same conversation thread, allowing reviewers to see the entire context of a conversation without having to review each email separately. This not only reduces the volume but enhances the relevance of the data by maintaining conversational context.
Domain and File Type Exclusions: Excluding certain domains or file types that are unlikely to contain relevant information can streamline the review process. For instance, excluding known spam domains or irrelevant file types like system files or executables can quickly reduce the dataset size.
Predictive Coding: Using advanced algorithms, predictive coding learns from decisions made on a set of reviewed documents to apply those decisions to a larger corpus. This method can effectively predict relevant documents, substantially reducing the need to manually review vast quantities of irrelevant data.
Importance of Effective Data Culling in Reducing Costs and Time
Cost Reduction: The costs associated with reviewing electronic data can be staggering, especially in large-scale litigations involving terabytes of data. Effective data culling directly impacts these costs by significantly reducing the volume of data that needs to be reviewed. Fewer data means less time required for review and lower costs for the manpower and technology needed to conduct it.
Time Efficiency: In the legal world, time is often of the essence. The quicker a case can move from discovery to trial or settlement, the better. By employing effective data culling techniques, legal teams can expedite the review process, enabling faster decision-making and progress in the case. This not only satisfies clients but also gives legal teams a strategic advantage by allowing them to focus on the case’s substantive issues sooner.
Enhanced Focus and Relevance: By removing irrelevant data early in the E-Discovery process, legal teams can focus on the most pertinent information. This enhances the overall quality of the review process, as reviewers are less likely to experience fatigue from sifting through large volumes of irrelevant data, which can lead to oversights.
Risk Mitigation: Effective data culling also plays a role in mitigating risks associated with data privacy and compliance. By reducing the dataset to only what is relevant, the exposure of sensitive information is minimized, which is crucial in adhering to privacy laws and regulations.
Conclusion
Legal data culling is a fundamental aspect of the E-Discovery process that, when executed effectively, can significantly reduce the cost and time associated with legal reviews. By integrating sophisticated culling techniques, legal teams can ensure that they are working with the most relevant and manageable dataset, which not only streamlines the discovery process but also enhances the quality of the legal analysis. As data volumes continue to grow, the role of effective data culling will become increasingly critical in managing the complexities of modern legal cases, underscoring the need for advanced solutions provided by experts like Relevant Data Technologies.
2.3 Data Indexing Services
Role of data indexing in improving data retrieval
Technologies used in indexing large data sets
In the intricate process of E-Discovery, where the efficient retrieval of relevant information is paramount, data indexing services play a critical role. These services facilitate quick access to required documents from vast digital archives, significantly improving the speed and accuracy of legal reviews. This detailed exploration will delve into the role of data indexing in enhancing data retrieval and the advanced technologies employed to index large data sets effectively.
Role of Data Indexing in Improving Data Retrieval
Data indexing is a systematic approach to organizing data in a way that makes information retrieval fast and efficient. In the context of E-Discovery, where legal teams often sift through terabytes of data, the importance of a well-structured index cannot be overstated. Indexing turns a chaotic collection of data into a neatly organized database, where every item is tagged and cataloged for easy retrieval.
Enhanced Search Capabilities: Through indexing, data is categorized using various metadata fields such as date, author, document type, and relevant keywords. This categorization allows users to perform precise searches that return relevant results swiftly. For instance, legal professionals can quickly locate all correspondences related to a specific topic within a defined time frame, dramatically cutting down the time spent manually searching through irrelevant documents.
Improved Efficiency and Productivity: With indexed data, the time taken to locate and retrieve information is significantly reduced. This efficiency boosts the productivity of legal teams, allowing them to focus more on analyzing the content rather than finding it. In high-stakes legal environments, this can be the difference between meeting and missing critical deadlines.
Scalability: Indexing supports scalability in data management. As legal cases evolve, so does the amount of data. Indexed systems are designed to accommodate growing data volumes efficiently without a drop in performance. This scalability ensures that the E-Discovery process remains robust and responsive, regardless of the size of the data set.
Technologies Used in Indexing Large Data Sets
The task of indexing large volumes of data requires robust technologies and sophisticated algorithms. Below are some of the key technologies that facilitate efficient data indexing in E-Discovery:
Database Management Systems (DBMS): Modern DBMSs are at the heart of indexing services. They are designed to handle vast amounts of data and support complex indexing schemes. These systems not only store data but also support powerful querying languages like SQL, which play a crucial role in retrieving indexed data efficiently.
Full-Text Indexing Tools: Tools such as Apache Lucene or Elasticsearch are widely used in E-Discovery for full-text indexing. These tools create extensive indexes that allow for quick full-text searches across large data sets. They are capable of handling complex queries, including fuzzy matching and proximity searches, which are essential for locating documents that contain similar or near-identical text strings.
Optical Character Recognition (OCR): OCR technology is used to convert scanned documents and images into machine-readable text. Once converted, this text can be indexed just like any other digital document. OCR extends the reach of indexing services to include non-digital documents, thus providing a comprehensive search capability across an entire data repository.
Artificial Intelligence and Machine Learning: AI and ML technologies are increasingly being integrated into indexing services to enhance the accuracy and efficiency of data categorization. These technologies can learn from data input and user interaction, continually improving the indexing process. For instance, machine learning algorithms can automatically categorize documents into relevant topics, further refining the indexing structure.
Cloud-based Indexing Solutions: With the rise of cloud computing, many E-Discovery platforms now offer cloud-based indexing solutions. These solutions provide the benefits of scalability, high availability, and reduced infrastructure costs. They also allow legal teams to access indexed data securely from anywhere, which is particularly beneficial for remote or distributed teams.
Conclusion
Data indexing services are indispensable in the realm of E-Discovery, providing a foundation for efficient information retrieval that can keep pace with the rapid acceleration and expansion of digital data in legal contexts. The technologies employed in data indexing not only streamline the retrieval process but also enhance the overall effectiveness of the E-Discovery phase. As data volumes continue to grow and the complexity of legal cases increases, the reliance on advanced data indexing services provided by experts like Relevant Data Technologies will only become more critical. These services not only save time and reduce costs but also improve the accuracy and outcomes of legal proceedings, making them an essential component of modern legal practice.
2.4 Document Coding for Litigation
Explaining the process and importance of document coding
How document coding facilitates easier data management and retrieval
In the complex and data-intensive environment of legal proceedings, the process of document coding for litigation emerges as a crucial strategy. This technique involves categorizing and indexing documents in a way that makes them easily retrievable for legal review and analysis. As legal cases involve the scrutiny of thousands, if not millions, of documents, document coding not only simplifies data management but also significantly enhances the efficiency of the E-Discovery process. In this detailed discussion, we will explore the process and importance of document coding, and examine how it facilitates easier data management and retrieval.
Explaining the Process of Document Coding
Document coding is a systematic method of organizing legal documents by assigning structured information to them, typically in the form of metadata tags. This metadata can include details about the document’s author, date of creation, document type, topics covered, and relevance to the case, among other things. Here’s a closer look at how this process is generally executed:
Document Collection: The first step involves collecting all the potential documents related to a case. This could include emails, memos, contracts, and other forms of correspondence.
Initial Review: Once collected, the documents undergo an initial review to assess their content and context within the litigation framework.
Creation of a Coding Scheme: Based on the initial review, a coding scheme is developed. This scheme determines the categories and tags that will be applied to the documents. The scheme can be customized to the specifics of the case to ensure all relevant information is captured.
Manual Coding by Trained Professionals: Trained legal professionals or paralegals usually carry out the coding. They review each document and assign codes according to the predefined schema. This task requires a deep understanding of the legal issues at stake as well as the details of the case.
Quality Control: To ensure accuracy, a secondary review is often conducted where a different team checks a sample of the coded documents against the original coding scheme.
Integration into E-Discovery Platforms: Once coding is complete, the coded data is uploaded into an E-Discovery platform like Relativity, where it can be easily accessed, searched, and analyzed.
Importance of Document Coding in Legal Contexts
Enhanced Searchability and Retrieval: Document coding transforms a haphazard pile of documents into a well-organized database where specific information can be retrieved swiftly via simple searches. This is particularly valuable in legal cases where time is of the essence and the ability to quickly find relevant documents can significantly influence the outcome of a case.
Increased Efficiency: By categorizing documents according to their relevance and type, legal teams can prioritize their review process, focusing first on the documents that are most likely to impact their case strategy. This targeted approach can lead to substantial time savings compared to a non-discriminative review of documents.
Cost Reduction: Document coding can also reduce costs associated with the review process. By eliminating or de-prioritizing irrelevant documents early on, the volume of documents that require detailed examination by high-level legal professionals is decreased, thus reducing the manpower and hours billed.
Consistency and Standardization: Document coding helps in maintaining consistency and standardization across all documents related to a case. This uniformity is crucial when multiple legal professionals are involved and ensures that everyone has the same understanding and information regarding the case.
How Document Coding Facilitates Easier Data Management and Retrieval
Structured Data Environment: Coding documents creates a structured data environment that simplifies the management of case documents. With each document tagged according to a specific criterion, organizing and retrieving data becomes a systematic process, governed by clear rules and parameters.
Integration with Legal Software: Coded documents can be seamlessly integrated with legal software systems that support advanced data analysis. These systems can utilize the coded metadata to perform complex analytical tasks, such as identifying patterns or predicting trends relevant to the case.
Support for Complex Litigations: In complex litigations involving multiple parties and voluminous data, document coding proves invaluable. The ability to quickly access and retrieve documents based on specific legal issues, parties involved, or chronological timelines can expedite the preparation and response strategies in ongoing litigations.
Conclusion
Document coding is a fundamental component of modern legal practices, especially in the context of litigation. By enabling efficient document management and easy retrieval of information, document coding not only streamlines the E-Discovery process but also enhances the overall strategic capabilities of legal teams. As legal proceedings continue to incorporate more digital data, the role of effective document coding will grow, further underlining its importance in achieving favorable legal outcomes. Companies like Relevant Data Technologies are at the forefront of providing expert E-Discovery and document coding services, ensuring that legal professionals can leverage the best tools and expertise in their legal endeavors.
Section 3: Forensic Data Collections and Analysis
3.1 Forensic Data Collection Services
Detailed methods used in forensic data collection
Importance of forensic accuracy and integrity
In the realm of legal disputes and investigations, the accuracy and integrity of data play pivotal roles. Forensic data collection is a critical phase in any investigative or legal process, where evidence must be handled with the utmost precision to maintain its admissibility in court. Forensic Data Collection Services provided by companies like Relevant Data Technologies specialize in capturing this data accurately and securely, ensuring that it stands up to the stringent scrutiny of legal proceedings. This comprehensive discussion will explore the detailed methods used in forensic data collection and underscore the importance of forensic accuracy and integrity.
Detailed Methods Used in Forensic Data Collection
Forensic data collection involves a series of specialized procedures designed to gather and preserve data in a manner that upholds its legal integrity. These methods are meticulously crafted to ensure data is accurate, complete, and untampered with throughout the legal process.
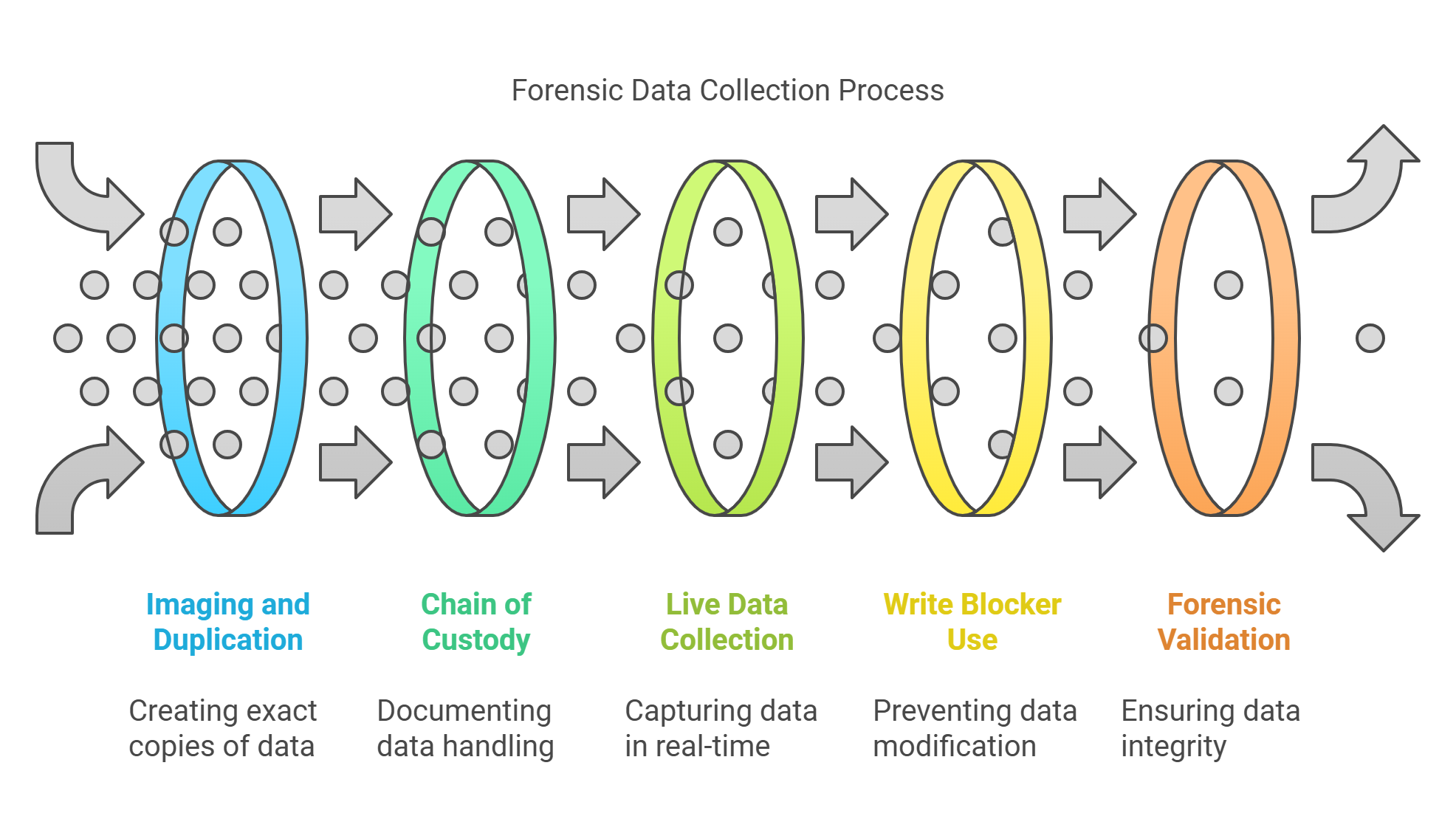
Imaging and Duplication: One of the first steps in forensic data collection is creating an exact bit-by-bit copy of the digital media, known as imaging or duplication. This process ensures that the original data remains untouched, and all investigations are conducted on the duplicate data. Tools like EnCase, FTK Imager, and dd are often used for this purpose, as they can create images that are forensically sound and include timestamps and hash values to verify the data’s integrity.
Chain of Custody Documentation: Maintaining a clear and detailed chain of custody is crucial in forensic data collection. This documentation logs every interaction with the data, from collection through analysis to presentation in court. It includes details about who accessed the data, when, and under what circumstances, ensuring that the evidence is handled consistently and transparently.
Live Data Collection: Sometimes, it’s necessary to collect data from systems that cannot be shut down or where the data might change if the system is powered off (like data in RAM). Live data collection techniques are used in these scenarios, employing specialized tools to capture the data without disrupting ongoing operations. This method is particularly important in corporate environments where server downtime is not feasible.
Use of Write Blockers: When accessing and copying data from storage devices, forensic professionals use write blockers—tools that allow data to be read from a device without the risk of writing any new data to it. This prevents accidental data modification and ensures that the forensic copy remains pristine.
Forensic Soundness and Validation: After data is collected, its forensic soundness must be validated. This often involves verifying cryptographic hashes taken before and after data collection to ensure that the copy is identical to the original. Validation procedures confirm that the tools and methods used during the collection did not alter the data, maintaining its integrity for legal scrutiny.
Importance of Forensic Accuracy and Integrity
Critical for Legal Admissibility: The ultimate goal of forensic data collection is to gather evidence that can be used in court. For evidence to be admissible, it must be collected and handled in a way that is legally sound and defensible. Any indication that data integrity has been compromised can lead to evidence being disallowed, which could severely impact the outcome of a case.
Establishing Trustworthiness: The accuracy and integrity of data not only support its admissibility in court but also the trustworthiness of the evidence. Accurate data collection helps to establish a clear and factual basis for legal arguments, aiding the justice system in making informed decisions. This is particularly vital in cases involving digital forensics, where data often holds the key to proving claims or defenses.
Preventing Spoliation: Accurate and careful data collection prevents the spoliation of evidence—where data is destroyed or significantly altered, accidentally or otherwise. Spoliation can lead to penalties, case dismissals, or adverse inference rulings, where the court assumes the destroyed evidence was unfavorable to the party responsible. Forensic data collection services prioritize the preservation of all data to avoid these legal pitfalls.
Supporting Higher-Stakes Decisions: In many legal cases, particularly those involving large corporations or serious criminal charges, the stakes are incredibly high. The accuracy and integrity of data collected can support decisions that have significant financial, legal, or personal consequences for the parties involved.
Conclusion
Forensic Data Collection Services are fundamental to the integrity of the legal process, ensuring that digital evidence is collected, handled, and preserved with the highest standards of accuracy. As technology evolves and digital data becomes increasingly central to legal proceedings, the demand for skilled forensic collection services will continue to grow. Companies like Relevant Data Technologies, which specialize in these services, play an essential role in the legal industry, providing the expertise and tools necessary to maintain the trustworthiness and admissibility of digital evidence.
3.2 Digital Forensics for Legal Cases
Applying digital forensics in the context of legal disputes
Case examples where digital forensics played a pivotal role
In the digital era, the realm of legal disputes has transcended physical evidence, embracing the vast and intricate world of digital data. Digital forensics has become an indispensable tool in modern litigation, providing crucial insights and evidence that can determine the outcomes of complex legal cases. This comprehensive exploration delves into how digital forensics is applied in legal disputes and highlights notable case examples where digital forensic expertise played a pivotal role.
Applying Digital Forensics in the Context of Legal Disputes
Understanding Digital Forensics: Digital forensics involves the recovery and investigation of material found in digital devices, often with the aim of using this data as evidence in a court of law. The discipline requires not only technical expertise to retrieve and preserve digital information but also legal knowledge to ensure that the evidence is admissible.
Methodologies Employed: The process typically starts with the identification of potential sources of digital evidence—computers, smartphones, cloud storage, etc. Forensic experts then follow a strict protocol to preserve the integrity of the data, which includes creating digital copies of the storage media (imaging) and documenting the chain of custody. The preserved data is then analyzed to reconstruct events or actions that are relevant to the case.
Tools and Technologies: Digital forensics uses a variety of tools to extract and analyze data. These include software like EnCase, FTK, and Cellebrite, which are capable of extracting data even from damaged or encrypted devices. Advanced techniques like cross-drive analysis can correlate information across multiple sources, and timeline analysis helps in reconstructing events as they unfolded.
The Role of Digital Forensics in Enhancing Legal Strategies
E-Discovery Compliance: In legal disputes, particularly those involving large corporations, compliance with E-Discovery requests is mandatory. Digital forensics experts ensure that all relevant digital data is identified, preserved, and reviewed in compliance with legal standards, thus safeguarding against potential sanctions or legal disadvantages.
Expert Testimony: Digital forensics professionals often provide expert testimony to explain the significance of digital evidence to the court or jury. Their insights can clarify complex technical details and help establish the relevance and implications of the digital evidence presented.
Case Examples Where Digital Forensics Played a Pivotal Role
Intellectual Property Theft: In a high-profile case involving a former employee accused of stealing trade secrets from a tech company, digital forensics experts were able to recover deleted files from the accused’s computer and external storage devices. The files contained proprietary code that was critical to the company’s operations. The forensic analysis not only proved that the employee had unlawfully copied and retained these files but also that they were transferred to a competitor. The evidence was instrumental in securing a conviction and subsequent damages for the company.
Financial Fraud Investigation: In a case of corporate fraud, digital forensic investigators analyzed email communications and financial transaction records stored on company servers. By using keyword searches and pattern recognition algorithms, they uncovered a hidden network of fraudulent transactions that had been cleverly masked by the company’s accounting team. The digital evidence led to the indictment of several high-ranking officials within the corporation.
Divorce and Custody Battles: Digital forensics is increasingly used in personal legal matters such as divorce and custody disputes. In one notable instance, forensics experts were able to recover incriminating text messages and emails from a spouse’s smartphone, which proved allegations of infidelity and misconduct. This evidence played a crucial role in the court’s decision regarding custody and division of assets.
Criminal Cases: In a landmark criminal case, digital forensics was used to convict a suspect based on digital evidence gathered from their social media and GPS data from their mobile device. The data placed the suspect at the crime scene at the time of the crime, corroborating other physical evidence and witness testimonies.
Conclusion
Digital forensics for legal cases is more than just a technical discipline; it is a cornerstone of modern legal processes. As digital devices continue to permeate every aspect of personal and professional life, the role of digital forensics in litigation will only grow in importance. For legal professionals and their clients, understanding and effectively leveraging digital forensics can mean the difference between winning and losing a case. Companies like Relevant Data Technologies play a crucial role in this landscape, providing the expertise and technological solutions necessary to navigate the complexities of digital evidence in legal disputes.
3.3 E-Discovery Forensic Analysis
Techniques and tools used in forensic analysis during E-Discovery
Bridging the gap between digital data and legal requirements
In the digital age, the intersection of technology and law becomes increasingly crucial, especially in the context of litigation and compliance investigations. E-Discovery forensic analysis plays a pivotal role in this intersection, providing the necessary tools and techniques to bridge the gap between vast amounts of digital data and stringent legal requirements. This article explores the sophisticated methods used in forensic analysis during E-Discovery and discusses how these methods meet legal standards, thereby ensuring that digital evidence is both compelling and compliant.
Techniques and Tools Used in Forensic Analysis During E-Discovery
E-Discovery forensic analysis involves a range of techniques and tools designed to identify, preserve, extract, and validate digital data that can be used in legal proceedings. The goal is not only to find relevant data but also to maintain its integrity in a legally acceptable manner.
Data Identification and Preservation: The first step in forensic analysis is to identify relevant sources of data. This might include hard drives, cloud storage, mobile devices, and even IoT devices. Once identified, the data must be preserved using forensic imaging techniques that create an exact, bit-for-bit copy of the data. Tools like FTK Imager and EnCase are commonly used for this purpose, as they ensure that the original data remains unaltered, preserving the metadata and reducing the risk of data tampering or loss.
Data Extraction: After preservation, the next step is extracting the data. This involves using software tools that can read the forensic images and extract usable information. Extraction must be done in a way that upholds the data’s authenticity and ensures it can be presented as evidence. Techniques such as keyword searches, hashing algorithms, and decryption are used to access and categorize the data effectively.
Data Analysis: Once data is extracted, it must be analyzed to determine its relevance to the case. Tools like Nuix and Relativity are used in this phase, offering advanced search capabilities, tagging, and categorization. These tools also allow for the analysis of patterns and relationships between data points, which can uncover insights that are not immediately obvious.
Reporting and Documentation: An essential part of forensic analysis is documenting the process and results. This documentation must be detailed and precise, as it may be scrutinized in legal proceedings. The reports generated should outline how the data was handled, analyzed, and how the conclusions were reached, ensuring transparency and adherence to legal standards.
Bridging the Gap Between Digital Data and Legal Requirements
Forensic analysis in E-Discovery is not just about managing digital data—it’s also about ensuring that this data can stand up to legal scrutiny. Bridging this gap requires a thorough understanding of both technical and legal aspects.
Compliance with Legal Standards: Forensic analysis must comply with legal standards such as the Federal Rules of Civil Procedure (FRCP) in the United States, which govern the handling of electronic evidence. This involves using tools and methods that are accepted in the legal community and that ensure the evidence is collected, processed, stored, and transferred in a secure manner.
Chain of Custody: Maintaining a clear and unbroken chain of custody is crucial in forensic analysis. This involves tracking the evidence from the moment it is collected until it is presented in court, with all transfers and accesses documented thoroughly. This ensures that the evidence has not been altered or tampered with and is therefore reliable.
Legal Admissibility: For digital evidence to be admissible in court, it must be relevant, authentic, and not overly prejudicial. Forensic tools must therefore be able to not only uncover relevant data but also provide metadata and other context that support its authenticity and relevance.
Data Privacy and Security: Forensic analysis must also consider data privacy laws, such as GDPR in Europe or CCPA in California. Analysts must ensure that personal data is handled according to these regulations, which may involve redacting personal information from documents before they can be used in litigation or ensuring that data transfers are secure and compliant.
Conclusion
E-Discovery forensic analysis is a critical field that requires a blend of technical expertise and legal acumen. As digital data becomes increasingly prevalent in legal disputes, the demand for skilled forensic analysts who can navigate both the digital landscape and the legal environment will continue to grow. Companies like Relevant Data Technologies are at the forefront of this field, providing the expertise and tools necessary to transform complex digital data into clear, comprehensible, and legally compliant evidence. By mastering the art and science of E-Discovery forensic analysis, legal professionals can ensure that they are fully prepared to handle the challenges of modern litigation.
3.4 Mobile Device Forensics in E-Discovery
Challenges and solutions in extracting data from mobile devices
Tools and technologies that enhance mobile forensics
In the realm of electronic discovery (E-Discovery), mobile device forensics represents a critical and complex frontier. As mobile devices have become ubiquitous, storing vast amounts of personal and professional data, they have also become key sources of evidence in legal disputes. However, extracting data from these devices poses unique challenges due to their diverse operating systems, security features, and the nature of mobile data. This detailed discussion explores the challenges in mobile device forensics, the solutions employed to overcome these obstacles, and the advanced tools and technologies that facilitate these processes in the context of E-Discovery.
Challenges in Extracting Data from Mobile Devices
Diversity of Devices and Operating Systems: One of the primary challenges in mobile device forensics stems from the sheer variety of devices and operating systems (OS), including iOS, Android, Windows, and others. Each OS has its security protocols and data storage formats, requiring forensic examiners to use specific strategies and tools for data extraction.
Encryption and Privacy Features: Modern mobile devices come equipped with robust encryption and privacy features designed to protect user data. Features like biometric locks, end-to-end encryption in messaging apps, and encrypted storage complicate the forensic extraction of data. Bypassing these security measures without altering the data can be particularly challenging.
Data Volatility: Mobile devices constantly receive and transmit data, and many types of data (such as location information or app data) are volatile, meaning they can be overwritten or lost swiftly. Capturing this data before it changes or disappears requires timely and precise forensic interventions.
Legal and Ethical Considerations: Mobile device forensics must navigate complex legal and ethical issues. Laws regarding privacy and data access vary by jurisdiction and must be carefully considered during forensic investigations to ensure that data collection complies with legal standards and respects user privacy.
Solutions in Mobile Device Forensics
To address these challenges, forensic experts employ a range of sophisticated techniques and strategies:
Advanced Data Extraction Methods: Forensic examiners use specialized methods to extract data from mobile devices. These include physical extraction, which accesses all data on the device including deleted files, and logical extraction, which copies all visible data. Chip-off and JTAG techniques may also be used for damaged devices or those with strong encryption.
Customized Tools for Different Operating Systems: Experts use different tools and software tailored to handle specific operating systems. For iOS, tools like XRY or Cellebrite can bypass certain security features to access data, while for Android, tools like Oxygen Forensic Detective are used to extract and analyze data more effectively.
Forensic Software Updates: As mobile technologies evolve, forensic tools are regularly updated to handle new security features and data formats. Keeping these tools updated is crucial for ensuring the effectiveness of forensic investigations.
Maintaining Chain of Custody: To preserve the integrity of data and ensure its admissibility in court, forensic experts meticulously document the chain of custody during the data extraction process. This includes detailed logs of how data was accessed, handled, and analyzed.
Tools and Technologies that Enhance Mobile Forensics
The field of mobile device forensics has seen significant advancements in terms of the tools and technologies used. These innovations enhance the ability of forensic experts to retrieve and analyze data efficiently:
Cellebrite UFED: This tool is widely regarded in the forensic community for its ability to perform comprehensive physical, logical, file system, and password extractions of all data from the widest range of mobile devices.
MSAB XRY: XRY extracts more data, in less time, with full integrity. It lets you access more data from smartphones, tablets, mobiles, GPS, drones and more.
Oxygen Forensic Detective: It offers advanced data extraction and analytical capabilities for mobile devices. It’s particularly useful for capturing data from a variety of apps and decrypting encrypted backups.
Magnet AXIOM: Known for its robust capabilities in smartphone forensics, Magnet AXIOM allows for the recovery and analysis of smartphone data, including artifact recovery from app data.
Encase Forensic: This tool is used for data investigation on smartphones and tablets, providing deep forensic analysis of user data.
Conclusion
Mobile device forensics is a critical component of modern E-Discovery, equipped to handle the challenges posed by the digital age’s mobile-centric data environment. As mobile devices continue to evolve, so too must the tools and techniques used in their forensic examination. The ongoing development of forensic technologies and methodologies ensures that legal professionals can continue to rely on mobile device data in their legal strategies, making it possible to uncover truth and uphold justice in an increasingly mobile world.
Section 4: Facilities Management and Document Solutions
4.1 Legal Facilities Management Services
Overview of facilities management in the legal sector
How outsourcing facilities management can benefit law firms
In the legal sector, the smooth operation of facilities plays a crucial role in ensuring that law firms can focus on their primary task—practicing law. Legal facilities management encompasses a wide array of services designed to manage the physical spaces and administrative functions that support legal professionals. As law firms seek to optimize their operations and reduce overhead costs, many are turning to outsourced facilities management solutions. This article provides an overview of facilities management within the legal sector and explores how outsourcing these services can significantly benefit law firms.
Overview of Facilities Management in the Legal Sector
Facilities management in the legal sector involves a comprehensive approach to managing the myriad support services that help a law firm run smoothly. This includes everything from building maintenance and security to information management and hospitality services. The goal of facilities management in this context is to create an optimal working environment that enhances productivity and enables lawyers to focus on delivering high-quality legal services.
Key Components of Legal Facilities Management:
Building and Grounds Maintenance: Ensures that the physical workspace is safe, clean, and well-maintained, which includes regular inspections and repairs, cleaning services, and landscaping.
Security Services: Provides security measures that protect the firm’s staff, clients, and sensitive information, encompassing everything from physical security guards to cybersecurity protocols.
Information Management: Manages the storage, retrieval, and disposal of legal documents securely and efficiently, ensuring compliance with legal regulations regarding document handling.
Technology Support: Ensures that all technological resources, such as computer systems, networks, and communication tools, are operational and up-to-date, minimizing downtime and supporting the firm’s capacity to engage in modern legal practices.
Hospitality and Client Care: Manages client-facing aspects of the firm’s operations, such as reception services, client meeting arrangements, and catering, enhancing the client experience and supporting business development efforts.
How Outsourcing Facilities Management Can Benefit Law Firms
Outsourcing facilities management offers several advantages that can lead to more efficient and cost-effective operations for law firms. As firms increasingly recognize these benefits, the trend towards outsourcing has grown.
Cost Efficiency: One of the primary benefits of outsourcing facilities management is reduced operational costs. Outsourcing allows law firms to convert fixed costs into variable costs, paying only for services as they are used rather than maintaining an in-house team. This not only reduces the need for large capital expenditures but also lowers ongoing expenses such as salaries, benefits, and training costs associated with full-time staff.
Access to Expertise: Outsourced providers specialize in managing facilities and bring a level of expertise that can be costly and difficult for law firms to develop internally. These providers stay up-to-date with the latest best practices, technologies, and regulatory changes, ensuring that the firm’s facilities are managed professionally and in compliance with all applicable standards.
Enhanced Flexibility and Scalability: Outsourcing facilities management provides law firms with the flexibility to scale their operations up or down as needed without the constraints of in-house resources. This is particularly beneficial for firms that experience seasonal fluctuations in workload or are undergoing growth and need to adapt their facilities management strategy quickly.
Improved Service Quality: Facilities management companies often have access to a wider network of vendors and can leverage economies of scale to secure services at lower costs and higher quality than individual law firms might be able to obtain on their own. This can lead to improved maintenance of the physical workspace and better overall service quality.
Focus on Core Business Activities: Perhaps most importantly, outsourcing facilities management allows law firms to concentrate on their core activities—practicing law and serving their clients. By alleviating the burden of managing non-core aspects of the business, lawyers can focus more on providing legal services, which can lead to better outcomes for clients and improved profitability for the firm.
Conclusion
In conclusion, legal facilities management services play a vital role in the smooth operation of law firms. Outsourcing these services offers numerous benefits, including cost savings, access to specialized expertise, and enhanced operational flexibility. As law firms continue to navigate the challenges of the modern business environment, the strategic management of facilities through outsourcing stands out as a smart choice for those looking to enhance efficiency and focus on their primary mission of legal advocacy.
4.2 Document Management Solutions
Innovative document management strategies
Impact of efficient document management on legal outcomes
In the legal sector, the ability to manage documents efficiently is not just a necessity but a strategic advantage. Document management solutions encompass a range of practices and technologies designed to organize, secure, and streamline access to documents. These solutions are particularly crucial in legal environments where the volume of documents can be overwhelming and where precision and quick access to information can significantly influence the outcome of cases. This article explores innovative document management strategies and examines the impact of efficient document management on legal outcomes.
Innovative Document Management Strategies
Digital Transformation: At the heart of modern document management strategies is the shift from paper-based to digital systems. This transition involves the use of advanced document management software (DMS) that not only stores documents digitally but also allows for sophisticated indexing and search capabilities. Tools such as version control, access logs, and automated workflows enhance the handling of documents, making them more accessible yet secure.
Cloud-Based Solutions: The adoption of cloud-based document management solutions has revolutionized how documents are stored and accessed in the legal field. These solutions offer scalable storage, remote access, and enhanced collaboration capabilities. Law firms can access case files and documents from anywhere, at any time, which is particularly beneficial in today’s increasingly mobile and remote work environments.
Automated Document Handling: Automation is a key strategy that is being increasingly integrated into document management systems. Automated workflows can handle tasks such as document filing, routing, and archiving without human intervention, reducing the risk of errors and increasing efficiency. Automation also includes the use of artificial intelligence (AI) to classify documents based on their content, suggest relevant documents during cases, and even predict document relevance based on past interactions.
Integrated Security Features: Given the sensitive nature of legal documents, security is a critical feature of any document management strategy. Modern DMS offer robust security features such as encrypted storage, role-based access control, and detailed audit trails that record every interaction with a document. These features ensure that confidential information remains protected from unauthorized access and comply with legal standards like GDPR and HIPAA.
Advanced Search and Retrieval Capabilities: Enhanced search functionalities are a hallmark of innovative document management. Using metadata tags, full-text search, and contextual filters, legal professionals can quickly find the documents they need, saving valuable time and increasing productivity. Advanced OCR (Optical Character Recognition) technologies also allow for the conversion of scanned images into searchable text, further easing the retrieval process.
Impact of Efficient Document Management on Legal Outcomes
Improved Responsiveness: Efficient document management systems enable law firms to respond more quickly to client needs and legal requirements. Faster document retrieval speeds up the preparation and filing of legal documents, which can be crucial during tight court deadlines or sudden legal disputes.
Enhanced Accuracy and Reduced Errors: By reducing reliance on manual document handling, efficient document management decreases the likelihood of errors such as misfiling or losing documents. Accurate, timely, and consistent document handling improves the overall quality of legal services provided.
Cost Efficiency: Effective document management reduces the need for physical storage and minimizes the administrative overhead associated with managing paper documents. It also cuts down the time spent by staff in organizing and searching for documents, allowing them to focus on higher-value tasks, thereby optimizing resource utilization and reducing costs.
Better Collaboration: In the legal world, cases often require collaboration among multiple stakeholders, including different departments within a firm, as well as external partners like opposing counsel or regulatory bodies. Efficient document management facilitates this collaboration by ensuring that all parties have timely and secure access to necessary documents.
Stronger Compliance and Risk Management: Proper document management ensures that law firms adhere to industry regulations concerning document handling and privacy. Compliance reduces legal risks associated with improper document management and helps in defending the firm if its practices are ever questioned.
Conclusion
Document management solutions are foundational to the success and efficiency of modern legal practices. By implementing innovative document management strategies, law firms can significantly enhance their operational effectiveness and improve legal outcomes. As technology continues to evolve, staying abreast of the latest developments in document management will remain crucial for law firms aiming to maintain competitive advantage and uphold the highest standards of legal service.
4.3 Secure Document Storage Solutions
Importance of security in document storage
Technologies and practices to ensure the protection of sensitive information
In today’s increasingly digital landscape, the importance of secure document storage solutions cannot be overstated, particularly for industries dealing with sensitive or confidential information, such as legal, healthcare, and financial services. As data breaches become more frequent and sophisticated, the need to protect sensitive documents from unauthorized access and ensure their integrity is crucial. This article explores the critical importance of security in document storage and delves into the cutting-edge technologies and practices designed to safeguard sensitive information.
The Importance of Security in Document Storage
Security in document storage is not just about protecting privacy; it also encompasses the integrity and accessibility of the stored information. In sectors like the legal field, where documents often contain sensitive data that could affect the outcome of litigation, or in healthcare, where patient records are confidential, ensuring document security is paramount.
Compliance with Regulations: Various regulations such as GDPR, HIPAA, and Sarbanes-Oxley impose stringent requirements on how organizations must manage and protect sensitive information. Secure document storage solutions help ensure compliance with these regulations, reducing the risk of costly penalties and damage to reputation.
Preventing Data Breaches: With the average cost of a data breach reaching millions of dollars, secure storage of documents is critical to mitigating financial risks. Effective security measures prevent unauthorized access to sensitive data, thereby protecting organizations from potential breaches and cyber threats.
Maintaining Client Trust: For many businesses, the ability to safeguard client information directly impacts their ability to maintain and build trust. In legal and financial services, where confidentiality is a cornerstone of client relationships, secure document storage is essential.
Technologies and Practices to Ensure the Protection of Sensitive Information
To address the challenges of document security, several advanced technologies and best practices have been developed. These tools not only enhance the security of document storage but also ensure that documents are accessible and manageable without compromising on protection.
Encryption: Encryption is one of the most effective technologies for protecting data. By encoding documents, encryption ensures that even if data is intercepted, it cannot be read without the encryption key. Full disk encryption and end-to-end encryption are commonly used methods to secure stored documents and data in transit.
Access Controls: Implementing strict access controls ensures that only authorized personnel can access sensitive documents. Techniques such as role-based access control (RBAC) and multi-factor authentication (MFA) are crucial in minimizing the risk of unauthorized access.
Data Loss Prevention (DLP) Technologies: DLP systems are designed to detect and prevent data breaches, data exfiltration, and unauthorized access to or sharing of sensitive information. They can be configured to automatically enforce policies for all documents stored within an organization’s network.
Cloud Storage Security: As more organizations move their document storage to the cloud, securing these environments has become imperative. Cloud storage providers typically offer robust security measures, including advanced encryption, physical security, and secure data centers. Additionally, they comply with major regulatory standards, which can help organizations meet their compliance obligations.
Regular Audits and Compliance Checks: Regular security audits and compliance checks are essential to ensure that document storage solutions continue to protect sensitive information effectively. These audits help identify vulnerabilities in the system and verify that all security measures are up to date.
Document Management Systems (DMS): Modern DMS offer built-in security features tailored for sensitive information management. These systems support compliance efforts through controlled access, audit trails, document versioning, and records of user activities, which are critical for tracing access and modifications to stored documents.
Physical Security: For physical document storage, security measures such as biometric access, surveillance cameras, and secured access to storage areas are vital. These measures protect against unauthorized physical access to sensitive documents.
Conclusion
Secure document storage solutions are essential for protecting sensitive information from cyber threats and ensuring compliance with regulatory standards. By integrating advanced technologies and best practices into their document management strategies, organizations can safeguard their data against unauthorized access and breaches. As technology evolves, staying abreast of the latest security trends and solutions will be crucial for organizations aiming to protect their critical information in the digital age.
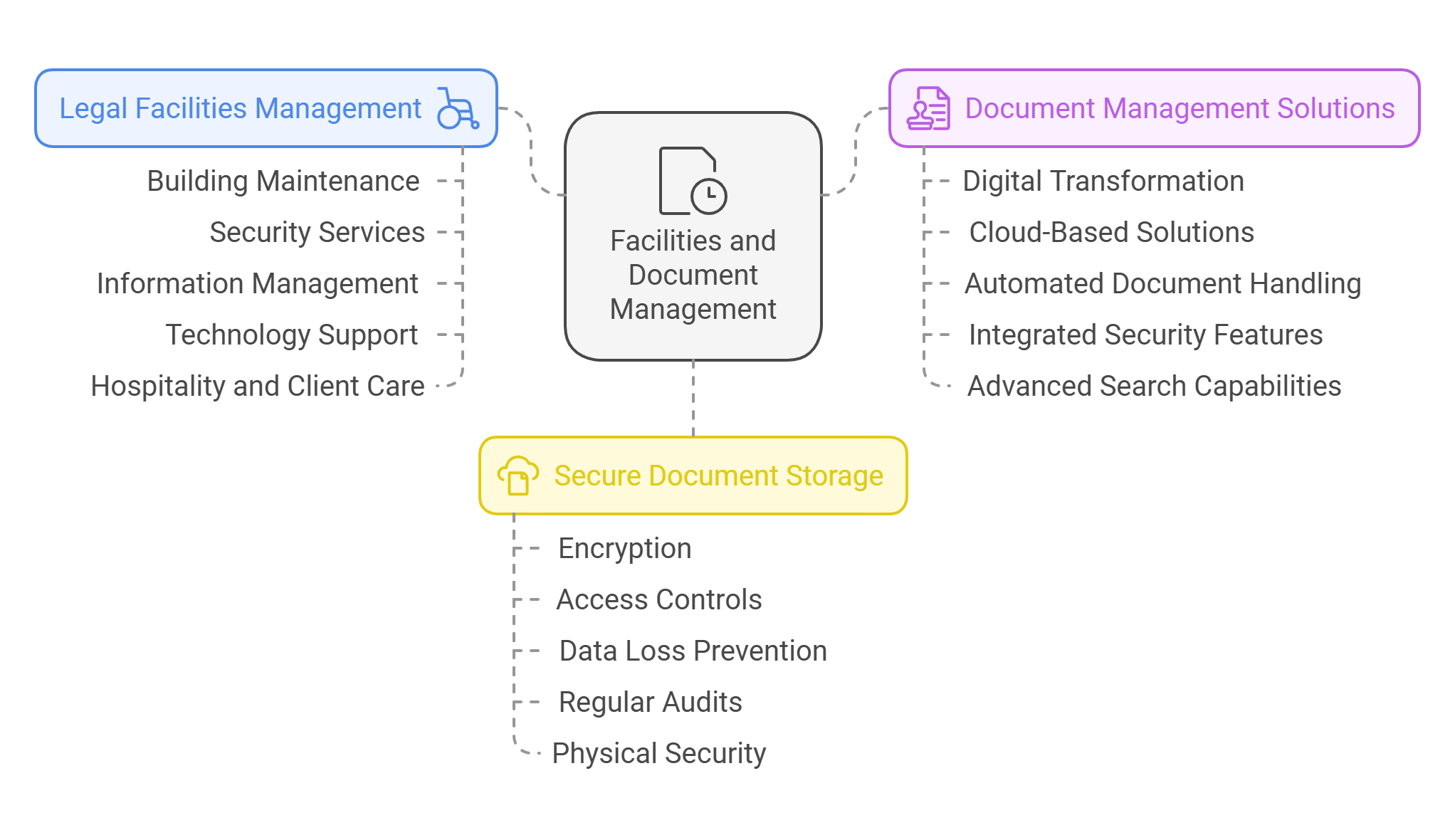
Section 5: Expert Report Writing and Testimony
5.1 Expert Witness Services for E-Discovery
Role of expert witnesses in interpreting E-Discovery findings
Training and qualifications of experts in E-Discovery
In the increasingly digital landscape of modern litigation, the role of expert witnesses in E-Discovery has become paramount. As legal disputes often hinge on complex electronic data, expert witnesses are vital in interpreting E-Discovery findings and providing clear, authoritative insights to courts. These experts not only help in understanding the nuances of digital evidence but also ensure that such evidence is presented in a legally sound manner. This article will explore the critical role of expert witnesses in E-Discovery, the specialized training and qualifications they possess, and how they influence the outcomes of legal proceedings.
The Role of Expert Witnesses in Interpreting E-Discovery Findings
Expert witnesses in E-Discovery are professionals with specialized knowledge in electronic discovery, digital forensics, and information technology. Their role is to interpret complex digital data and provide an independent opinion on the findings in a manner that judges and juries can comprehend.
Clarifying Complex Technical Issues: One of the primary roles of an E-Discovery expert is to demystify complex technical data for the court. This may involve explaining how data was preserved, retrieved, and analyzed, as well as the significance of digital evidence within the context of the case.
Validating the E-Discovery Process: Expert witnesses ensure that the methods used to collect and analyze electronic data adhere to accepted standards. They assess the E-Discovery process for compliance with legal requirements and best practices, helping to prevent the disqualification of digital evidence on the grounds of improper handling or bias.
Impact on Legal Strategies: Expert witnesses in E-Discovery can significantly impact legal strategies. Their insights can validate or challenge the integrity of data presented in court, influencing key aspects of a case such as the credibility of evidence or the intent behind actions captured in digital records.
Providing Testimony: Beyond technical analysis, expert witnesses may be called to testify in court. Their testimony can provide crucial support for a case, offering clear explanations of technical evidence and persuading judges and juries of their conclusions.
Training and Qualifications of Experts in E-Discovery
The effectiveness of an expert witness in E-Discovery largely depends on their training and qualifications. These professionals typically possess a blend of technical knowledge, practical experience, and understanding of legal processes.
Educational Background: A strong academic background in computer science, information technology, or cybersecurity is common among E-Discovery experts. Advanced degrees in these fields provide a solid foundation for understanding the complex technologies involved in E-Discovery.
Professional Certifications: Certifications specific to E-Discovery and digital forensics add to an expert’s qualifications. Certifications such as the Certified Information Systems Security Professional (CISSP), Certified E-Discovery Specialist (CEDS), or Certified Forensic Computer Examiner (CFCE) demonstrate a recognized level of expertise and commitment to the field.
Legal Knowledge: Understanding the legal aspects of E-Discovery is crucial. Experts often pursue additional training or qualifications in law, particularly areas relevant to electronic evidence. This includes familiarity with the Federal Rules of Civil Procedure, privacy laws, and regulations governing digital data.
Practical Experience: Hands-on experience in managing E-Discovery projects in legal settings is invaluable. Experience provides experts with practical insights into the challenges and nuances of the field, enhancing their ability to address complex issues effectively in court.
Continuing Education: Given the rapid pace of technological change, ongoing education is essential for E-Discovery experts. Regular training helps them stay updated on the latest tools, techniques, and legal developments in E-Discovery.
Conclusion
Expert witness services in E-Discovery are critical to navigating the complexities of modern litigation involving digital data. By providing expert interpretations of electronic findings and validating the processes used to secure and analyze data, these professionals play a pivotal role in ensuring the integrity and admissibility of digital evidence. The qualifications and training of these experts directly impact their ability to contribute effectively to legal cases, making their expertise indispensable in the judicial consideration of digital records. As technology continues to evolve and become more integral to legal proceedings, the demand for skilled E-Discovery expert witnesses will undoubtedly increase, further emphasizing the need for continuous professional development in this dynamic field.
5.2 Forensic Expert Report Writing
Crafting detailed and comprehensible forensic reports
Standards and expectations for forensic reporting in legal contexts
In the realm of legal proceedings, the forensic expert report serves as a crucial document that bridges complex forensic analysis with judicial review. Crafting detailed and comprehensible forensic reports is an art that requires not only deep technical knowledge but also an understanding of legal expectations and standards. This detailed discussion explores the intricacies of forensic expert report writing, outlining the meticulous process involved and the rigorous standards that these reports must meet to be effective in legal contexts.
Crafting Detailed and Comprehensible Forensic Reports
Forensic expert reports translate complex data into a format that can be understood and utilized by attorneys, judges, and juries. The ability to convey intricate information clearly and effectively is paramount, as these reports can significantly influence the outcome of legal proceedings.
Structure and Clarity: A well-structured forensic report begins with a clear introduction that outlines the scope of the investigation, followed by a detailed methodology section that explains how the forensic analysis was conducted. This is crucial for establishing the reliability of the findings. The body of the report should then present the data in a logical order, using clear, concise language to explain the findings and their implications.
Use of Visuals and Appendices: To enhance comprehension, forensic reports often include visual aids such as charts, graphs, and diagrams. These tools can help illustrate complex data points and show relationships or patterns that support the report’s conclusions. Additionally, appendices can provide raw data or detailed calculations that support the report’s findings but are too voluminous to include in the main body of the text.
Objective and Unbiased Tone: It is essential for forensic reports to maintain an objective and unbiased tone throughout. The expert’s role is to present the facts as they are, not to advocate for one side of the litigation. The use of neutral language helps ensure that the report is viewed as credible and professional.
Thorough Documentation: Every assertion or conclusion in the report should be backed by data or accepted forensic methodologies. Thorough documentation and citation of sources, whether it’s case law, statutes, or scientific principles, are crucial for bolstering the report’s credibility and utility in legal proceedings.
Standards and Expectations for Forensic Reporting in Legal Contexts
Forensic reports must adhere to high standards of accuracy, reliability, and relevance to be considered valid in a legal context. Understanding these standards and expectations is vital for forensic experts who wish to produce effective reports.
Adherence to Legal Standards: Forensic reports must comply with specific legal standards and rules of evidence. In the United States, this often means alignment with the Federal Rules of Evidence, particularly with respect to the admissibility of expert testimony and scientific evidence. Reports should be prepared with these rules in mind to ensure that they withstand legal challenges.
Reliability and Validity: The methodologies used in the forensic analysis must be proven to be reliable and valid. This means they should be generally accepted in the expert’s professional community and capable of being replicated. This aspect of the report is often scrutinized during Daubert hearings, where the admissibility of expert testimony is evaluated.
Transparency and Reproducibility: Forensic reports should be transparent in the methods used and data obtained so that another expert could reproduce the results using the same procedures. This transparency not only enhances the report’s credibility but also its scientific and legal acceptability.
Ethical Considerations: Experts must adhere to the highest ethical standards when conducting forensic analysis and writing reports. This includes maintaining confidentiality, avoiding conflicts of interest, and ensuring that their findings are based solely on the evidence and their professional expertise.
Conclusion
Forensic expert report writing is a critical skill in the field of forensic analysis, particularly when the findings are to be presented in legal contexts. These reports must be meticulously crafted, with attention to detail and a clear, comprehensible format that can be understood by non-experts. Additionally, they must meet strict legal and professional standards to ensure that they are both admissible and effective in influencing the outcomes of legal cases. As the intersection of law and forensic science continues to evolve, the demand for high-quality forensic reporting will only grow, underscoring the need for ongoing training and development in this challenging yet vital discipline.
5.3 Digital Evidence Expert Testimony
Preparing and presenting digital evidence in court
Enhancing the credibility of digital evidence through expert testimony
In today’s digital age, where technology permeates almost every aspect of life, digital evidence has become a cornerstone in both criminal and civil litigation. As such, the role of digital evidence expert testimony is critical in clarifying the complexities of digital data for courts and juries. Expert testimony on digital evidence involves meticulously preparing and presenting data so that it is understandable and carries weight in legal decisions. Furthermore, the credibility of this evidence can significantly influence the outcome of a case, making the expertise and presentation skills of the witness vital. This article explores the processes involved in preparing and presenting digital evidence in court and the methods used to enhance its credibility through expert testimony.
Preparing and Presenting Digital Evidence in Court
The process of presenting digital evidence in court is meticulous and demands both technical knowledge and an understanding of legal processes. Here’s how experts prepare and present digital evidence effectively:
Collection and Preservation: The first step involves the accurate collection and preservation of digital evidence. This must be done in a manner that prevents data tampering or loss. Experts use forensically sound methods to extract data from various devices, ensuring all actions are logged and the chain of custody is maintained.
Analysis and Interpretation: Once the data is securely collected, it undergoes a detailed analysis. Experts use various software tools to sift through the data, identify relevant information, and interpret the findings. This stage is crucial, as the interpretation must be accurate and reflect the evidence’s context within the case.
Report Preparation: After analysis, experts prepare detailed reports that summarize the findings. These reports should be clear and structured, providing descriptions of how the evidence was collected, analyzed, and its relevance to the case. The reports often include visual aids like charts, graphs, and diagrams to help explain complex data clearly.
Pre-Trial Consultation: Before appearing in court, digital evidence experts often consult with the legal team to align the evidence presentation with the overall case strategy. This may involve mock trials or direct discussions on how to handle potential cross-examinations.
Testimony in Court: In court, experts must present their findings in a way that is understandable to those without technical backgrounds. They need to explain complex technical processes clearly and concisely, often answering questions from both the defense and prosecution. The ability to communicate effectively under oath is as crucial as the technical expertise itself.
Enhancing the Credibility of Digital Evidence Through Expert Testimony
The credibility of digital evidence can significantly affect its impact on a trial’s outcome. Here are ways in which expert testimony enhances the credibility of digital evidence:
Demonstrating Expertise: The expert’s background, experience, and qualifications are often presented early in their testimony. This establishes their authority and expertise, which enhances the weight of their conclusions. Relevant certifications, education, and practical experience in digital forensics can reinforce the trustworthiness of their testimony.
Transparent Methodology: By clearly explaining the methods used to collect and analyze digital evidence, experts can demonstrate that their findings are based on reliable and accepted practices. This transparency helps the court understand the processes involved and the reasons for the expert’s conclusions, thus enhancing the evidence’s credibility.
Handling Cross-Examination: The ability to maintain composure and credibility during cross-examination is crucial. Experts must be prepared to defend their methodologies and findings rigorously. Effective handling of cross-examination often involves anticipating opposing arguments and preparing clear, concise responses.
Ethical Standards: Adherence to ethical standards in digital forensics is essential for credibility. Experts must handle all evidence and related processes ethically, avoiding any actions that could be perceived as biased or manipulative. Ethical lapses can severely damage the credibility of the evidence and the expert’s testimony.
Peer-Reviewed Techniques: Using techniques and tools that are peer-reviewed and widely accepted in the field of digital forensics lends additional credibility to the expert’s findings. The use of established, scientifically validated methods reassures the court of the evidence’s reliability.
Conclusion
Digital evidence expert testimony is a pivotal element in modern litigation, bridging the gap between complex digital data and judicial decision-making. By effectively preparing, presenting, and enhancing the credibility of digital evidence, experts play a critical role in ensuring that this type of evidence is both understandable and persuasive in court. As technology continues to evolve, so too will the strategies and techniques used in digital evidence presentation, making continuous learning and adaptation essential for experts in this dynamic field.
Conclusion
Summarizing the indispensable role of Relevant Data Technologies in providing comprehensive E-Discovery services that cater to the modern demands of litigation, compliance, and investigations. Highlighting the expertise, technological assets, and client-focused services that make Relevant Data Technologies a leader in the field.
In the complex terrain of modern litigation, compliance, and investigations, the role of advanced E-Discovery services becomes paramount. Relevant Data Technologies (RDT) stands at the forefront of this field, offering unparalleled expertise and technology-driven solutions tailored to the evolving needs of global clients. This article delves into the indispensable role of RDT in transforming E-Discovery processes, emphasizing its robust technological infrastructure, deep expertise, and client-centric approach that make it a leader in the industry.
Comprehensive E-Discovery Services
Relevant Data Technologies offers a full spectrum of E-Discovery services designed to streamline the discovery process, reduce costs, and enhance the accuracy of legal outcomes. These services are critical in today’s digital age where data is vast and verification needs to be both precise and efficient.
Data Collection and Processing: RDT uses state-of-the-art tools to collect data from a wide array of digital sources, including cloud storage, emails, and physical devices. This data is then processed with advanced algorithms to identify and categorize relevant information, making it ready for review.
Advanced Data Review: Leveraging cutting-edge software solutions, RDT provides sophisticated data review services. This includes predictive coding and other forms of artificial intelligence to help legal teams quickly sift through millions of documents and pinpoint critical pieces of information.
Legal Hold and Data Preservation: Understanding the critical nature of data integrity, RDT implements stringent legal hold procedures and data preservation strategies to ensure that all information is maintained in a forensically sound manner, thereby upholding its admissibility in court.
Expertise in Legal and Regulatory Compliance
RDT distinguishes itself by not only managing data but also ensuring that every step of the E-Discovery process is in compliance with pertinent legal and regulatory frameworks. This expertise is crucial for clients operating across various jurisdictions.
Global Compliance: From GDPR in Europe to HIPAA in the United States, RDT’s services are designed to meet the strictest legal and compliance standards globally. This comprehensive understanding of international law is vital for multinational corporations dealing with cross-border litigation and investigations.
Consultative Approach: RDT acts as a partner to its clients, offering expert consultations to navigate the complex landscapes of legal regulations. This involves advising clients on best practices for data management and compliance, significantly reducing the risk of legal penalties.
Technological Assets and Innovation
At the heart of RDT’s success are its technological assets and commitment to innovation. The company invests heavily in developing and acquiring the latest technologies to enhance its E-Discovery offerings.
Cutting-edge Software and Tools: RDT utilizes a suite of advanced software solutions, including Relativity for data review and management, which provides an intuitive platform for handling large datasets efficiently. Additionally, proprietary tools developed in-house offer customized solutions that address unique client needs.
Security Protocols: With robust security measures in place, RDT ensures the utmost protection of sensitive data. This includes encryption, multi-factor authentication, and continuous security monitoring to guard against both internal and external threats.
Cloud-based Solutions: Embracing the cloud, RDT offers scalable and flexible E-Discovery solutions that allow for remote access and collaboration. This is particularly beneficial in a globalized world where legal teams and stakeholders are often dispersed across various locations.
Client-Focused Services
Understanding that each client has unique needs, RDT prides itself on its client-focused approach, offering tailored solutions that ensure client satisfaction and loyalty.
Customization: RDT’s solutions are highly customizable, designed to fit the specific needs and preferences of each client, whether it’s a multinational corporation, a small law firm, or a government agency.
Support and Training: RDT provides ongoing support and training for all its solutions, ensuring that clients can leverage the full power of their E-Discovery tools. This includes dedicated customer service teams and comprehensive training modules.
Strategic Advisory: Beyond technical support, RDT offers strategic advisory services to help clients optimize their legal processes and outcomes. This includes workflow design, case strategy support, and risk management consulting.
Relevant Data Technologies is not just a provider of E-Discovery services; it is a strategic partner that enhances the legal capabilities of its clients through technology and expertise. By integrating comprehensive data management solutions, adhering to rigorous compliance standards, and maintaining a client-focused approach, RDT helps navigate the complexities of modern legal challenges. As the digital landscape continues to evolve, the role of RDT will undoubtedly grow, further cementing its status as a leader in the E-Discovery field.